Secure Your SaaS Stack in 30 Minutes.
Eliminate the critical blind spots of Non-Human Identities and complex permissions with the first European-sovereign platform for SaaS Authorization Management and Identity Threat Detection. Stop guessing who can access your most sensitive data and start seeing the full picture.
Start with a comprehensive, privacy-preserving audit — deployed in minutes.
Total Visibility.
Intelligent Defense.
Secure your entire identity fabric—human, machine, and AI—with one unified platform.
ISPM
Identity Security Posture Management. Proactively manage your identity attack surface and gain visibility into permissions and configurations.
- Continuous posture assessment
- Misconfiguration detection
- Least privilege enforcement
ITDR
Identity Threat Detection & Response. Stop identity threats before they become incidents by detecting suspicious privileges and abnormal behaviors in real-time.
Blast Radius & Exposure
Visualize and reduce the impact of potential breaches. Map identity relationships and limit lateral movement paths to critical assets.
- Identity graph visualization
- Lateral movement analysis
- Impact radius reduction
One Intelligence Layer.
Three Pillars of Defense.
From raw identity signals to automated security outcomes in milliseconds.
How Cydenti Works
From raw signals to actionable intelligence in milliseconds.
SaaS Apps
OAuth Apps
Identity Provider
Normalization
Posture Analysis
Identity Graph
Real-time Context
Detection Logic
Risk Engine
AI & LLMs That Actually
Understand Identity.
Cydenti uses in-house LLMs and AI agents to read identity behavior, SaaS posture, cloud permissions, and risky integrations — privately and securely.
- Spots configuration drift instantly
- Flags anomalies in behavior
- Reveals hidden access paths
Automation That
Removes Complexity.
Risk scoring, configuration checks, permission mapping, alert enrichment, and audit reporting — all automated.
Stop Threats That
Others Miss.
Cydenti observes authentication events, applies behavioral analytics, and flags anomalies in real-time. From credential stuffing to MFA fatigue, stop attacks before they become incidents.
User "jdoe" denied 15 push notifications in 2 minutes.
Logins from NY and Tokyo within 1 hour.
Access Explorer
Visualize every connection, permission, and identity path in real-time.
Discover
Ingest identity signals & build the graph
Assess
Score risk & map hidden paths
Remediate
Fix permissions & guide owners
Monitor
Continuous drift detection
Understanding
Blast Radius.
Blast radius is the total potential damage a compromised identity can cause. It's not just about what they should access, but everything they can access through hidden paths, group inheritance, and role assumption.
Mini Case Study: The "Luca" Scenario
Luca is a summer intern. He needs access to Jira and Slack. But because he was added to the DevOps group for a quick fix, he inherited:
- Shadow Admin rights on AWS Production
- Write access to Customer Database
The Fix: Cydenti detects this toxic combination immediately. We visualize the path, quantify the impact, and recommend removing the redundant group membership while keeping his necessary app access.
Identity Security Posture-Built for SaaS and Cloud
Most tools focus on logs, infrastructure, or governance workflows. Cydenti focuses on the root problem: identity risk, where modern breaches begin.
Identity Security Posture Management
Automated configuration checks for M365, Salesforce & more.
Identity Threat Detection and Response
Detect active threats and anomalies in real-time.
Blast Radius
Visualize and reduce blast radius across multi-cloud.
Identity Risk Scoring
Quantify risk for every human and machine identity.
Integrates with your SaaS and cloud stack
API-based integrations across Microsoft 365, Google Workspace, Salesforce, AWS IAM, Azure AD, GCP IAM, GitHub, Slack, and ServiceNow. Deployed in minutes.
Community & Gallery
Stay connected with our latest research, insights, and community discussions.
Frequently Asked Questions
Everything you need to know about Cydenti's SaaS Identity Security platform, from deployment to compliance.
Platform Overview
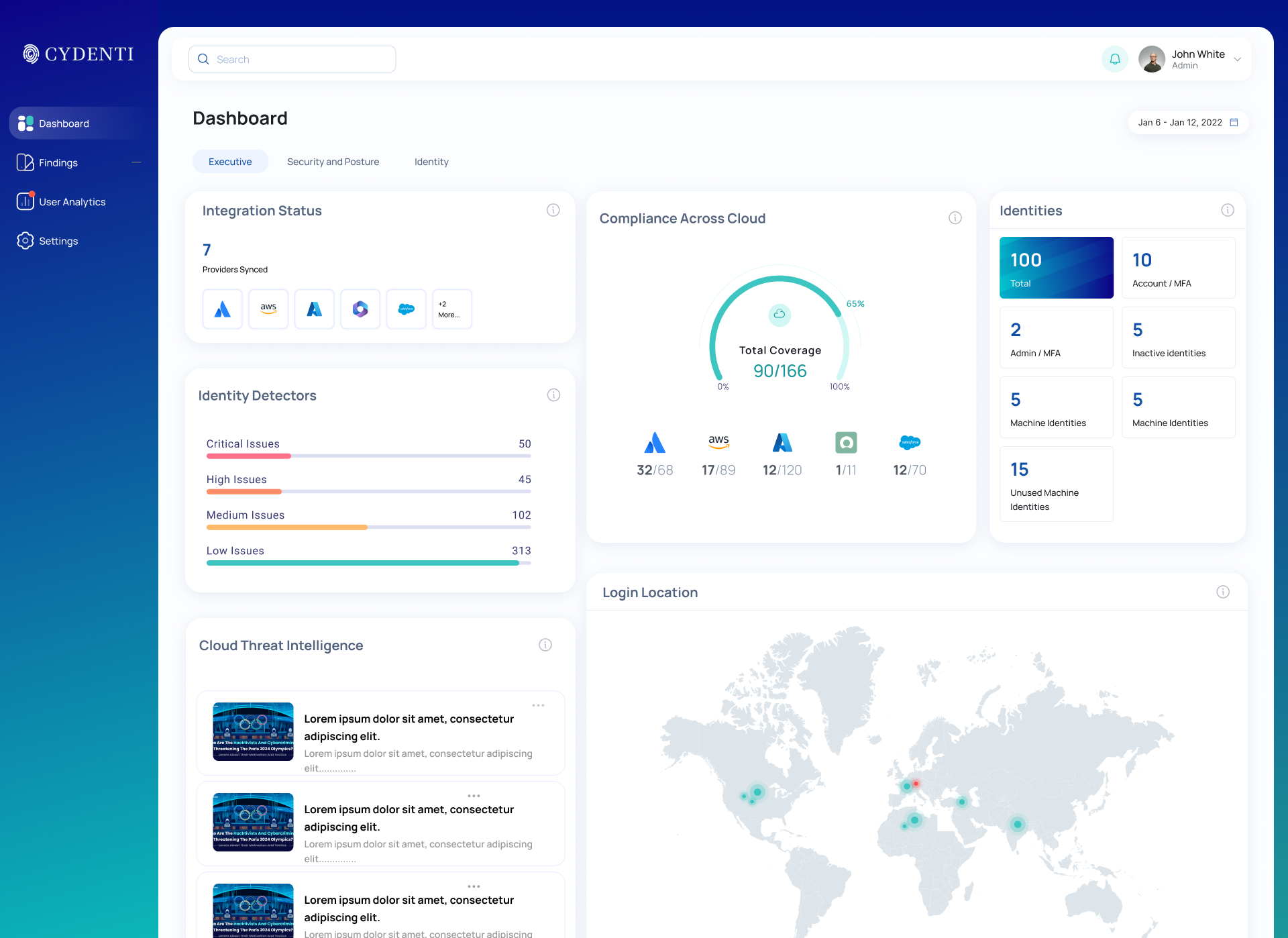
See your identity attack surface with
AI-powered clarity.
Across humans, machines, and AI agents. Cydenti delivers the visibility, intelligence, and automation needed to secure SaaS- and cloud-driven enterprises.